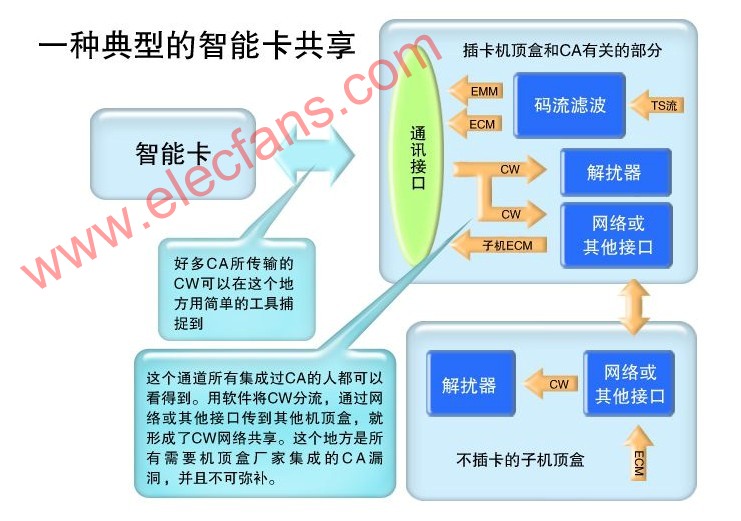
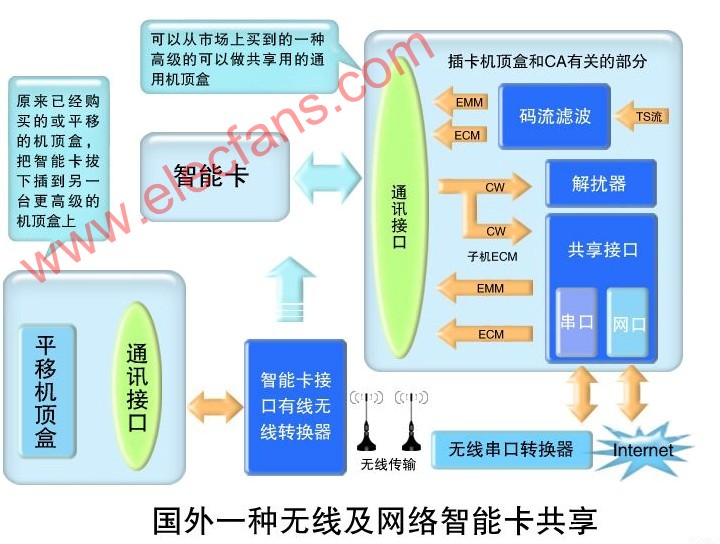
The various parts of the digital TV CA are closely connected. Once a part of the problem occurs, other parts will also be implicated. The cracking of CA starts from partial cracking, and is finally completely cracked. According to the CA process that has been cracked from the past, it is explained as follows: First of all, we must understand the structure of CA, see the smart card in Figure 1, which stores all the belongings of CA company. It also indicates the general importance of each part. Algorithms: The level of algorithm design in this part can determine the cost of smart cards. If you can design an efficient algorithm, you can reduce the requirements for smart cards. The cost of smart cards is high. Conversely, the cost of smart cards is low; but most of the core algorithms of CA companies It is 3DES or even DES, because the calculation of the DES algorithm in the smart card is time-consuming and requires high design. It is also for this reason that for the same CA company, the smart cards supplied in batches must be the same algorithm. DES (Data Encryption Standard) was recognized by the American National Standards Institute in 1977 as the standard for balanced encryption algorithms. It is an open algorithm and is still widely used until now. The descrambler used to decrypt the stream in the set-top box is also the DES algorithm. CAs that use algorithm secrecy generally add a shell to DES or 3DES, which plays a role of algorithm secrecy, but after this function is cracked in the communication interface, some high-level hackers can use plaintext and ciphertext. Regular correspondence, peel off this shell. Key: This part is generally set separately according to different operators, and some CA companies use the same set of keys for many small-scale operators. In the case of DES or 3DES, the key length is 64 bits, 8 check bits are removed, and the actual length is 56 bits. This key length indicates the possibility of a huge number of keys. In the beginning when the DES standard was used, it would take hundreds of years for an ordinary PC to crack a DES key. Thanks to the acceleration of the calculation speed, as early as 1998, someone made a machine dedicated to cracking des. This machine is called Deep Crack. It costs a total of 200,000 US dollars and averagely cracks (exhaustively) a correct key. It takes about 4 days. Even now, cracking such a machine would cost more than US $ 10,000 to manufacture such a machine. There are also reports abroad that using a high-speed DSP or FPGA costs less than $ 5,000 and can exhaust more than 100 billion keys per second, so that the correct key can be found within a few days. However, if there are enough plain text and cipher text for the template, many people use the PC to cooperate and use the collision method, and it is also possible to find the correct key in a short time. Although the data volume of the key is not large, its position in the CA is very important. After knowing but knowing the algorithm adopted by the CA, even if the smart card is not destroyed, it is only a matter of time before the key is released. The communication interface includes the following two parts: 1. COS interface, which is the interface necessary for CA company to develop CA, and is also the interface to write algorithm and key to the smart card, which is the same in every smart card. 2. The communication and command interface for communicating with the algorithm key is to send the ECM received by the set-top box to the algorithm part, and obtain the corresponding key according to the index for decryption. The communication interface is the closest part to the key and algorithm. After the communication interface is cracked, sufficient pairs of plaintext CW and ciphertext ECM can be obtained, which is beneficial to teamwork to obtain the key by collision method, which is a great threat to the digital TV CA that adopts key confidentiality measures. On the other hand, hackers can use the communication interface that has been cracked to further attack the algorithm in the smart card. Figure 2 is a traditional CA algorithm cracking method, which uses a physical method to read out the algorithm and key inside the smart card, and then copy the pirated card. Because the cost is relatively large, and the current CW network sharing cost is very low, in general, this method is no longer cracked. However, when the Internet was underdeveloped, almost all the first-generation CAs were cracked in this way. This was a very thorough crack, and the only solution was to change the card. Figure 3 shows the CA principle and cracking of CW encrypted transmission. Some CAs are encrypted in the CW transmission structure, but this encryption hardly hinders hackers. Figure 4 is the earliest and most popular network sharing technology. The most famous one is the Dream series satellite sharing set-top box produced in Germany. The current Dream series set-top box also has a very powerful PVR function. It uses the open Linux operating system. Popularizing digital TV sharing technology has played a big role. Currently, DreamBox is widely used in Europe and North America for smart card sharing. Dream also designed DreamBox500C specifically for the Chinese market because of its high price and few users. The second is South Korea ’s shared set-top box, which has a very high level of technology. They even use satellite transponders to provide shared services in areas with underdeveloped networks. Figure 4 Figure 5 is a more advanced smart card sharing, this sharing is most suitable for China's cable TV smart card sharing after translation. The method is to unplug the original set-top box and insert it into the shared set-top box, then insert a smart card to wireless adapter board into the original translation set-top box, and then insert a small box of wireless to serial port on the shared set-top box. In this way, the original panning set-top box becomes a slave machine, and the shared set-top box becomes a master machine. There is also a network interface on the master machine, which can be shared in a larger range of the Internet. When the original network was underdeveloped, the communication interface between the smart card and the set-top box only accounted for 30% of CA's possessions. If you take into account the development of the network, it will account for more than 50% of CA's possessions within two to three years. The more developed the network, the higher the program cost, and the lower the cost of the set-top box, this part poses a greater threat to CA companies and operators. Figure 6 shows the cracking steps of the traditional CA. As long as the decrypted CW algorithm is broken, the entire CA is finished, and the algorithm cracking in Figure 2 and the network sharing in Figure 4 and Figure 5 can be completed on this basis. Figure 6 In the above-mentioned cracking steps, the cracking of the first step (Step1) will not cause hidden dangers in the case of an underdeveloped network, and the cost will not be large, because a smart card needs to be inserted to unlock the program, and the cracking gain is not large. However, with the development of the Internet today, this step of cracking is of great significance, and has become the main form of digital TV piracy. The second step (Step2) is more expensive to crack and is the main form of digital TV piracy in the past. The cracker sells the CA algorithm to make huge profits. Because the piracy of Step 1 is easy to implement, and it is easy to share on the network, the significance of this expensive piracy is reduced. Piracy is an illegal act. Why is digital TV sharing piracy so common in Europe and the United States with strict laws? This is because the current set-top box technology in foreign countries has been very developed, and the network function is very powerful. For example, DreamBox in Germany is a "bare metal" with no sharing function at the factory. Users can download the software that can be shared by CW from the network after purchase. And because the software operating systems of these set-top boxes are mostly LINUX operating systems, to comply with the GPL (Open Public General Public License, General Public License), so the source code must be disclosed, many hackers have developed a variety of CW on this platform Shareware is very rich. Users who buy such machines can load CW shareware by themselves. In this way, CW sharing piracy of digital TV becomes a personal behavior of users. Here, a set-top box is like a PC in the ordinary sense. A user buys a set-top box just like a PC. It is the buyer ’s freedom to run and develop what kind of software to run on. There is no need for the person selling the set-top box to be responsible. This is the same reason that you buy a PC for bad things, and the responsibility is not on the person selling the PC. Portable Hotel Projector,home bedroom hotel projector,large banquet hotel projector Shenzhen Happybate Trading Co.,LTD , https://www.szhappybateprojectors.com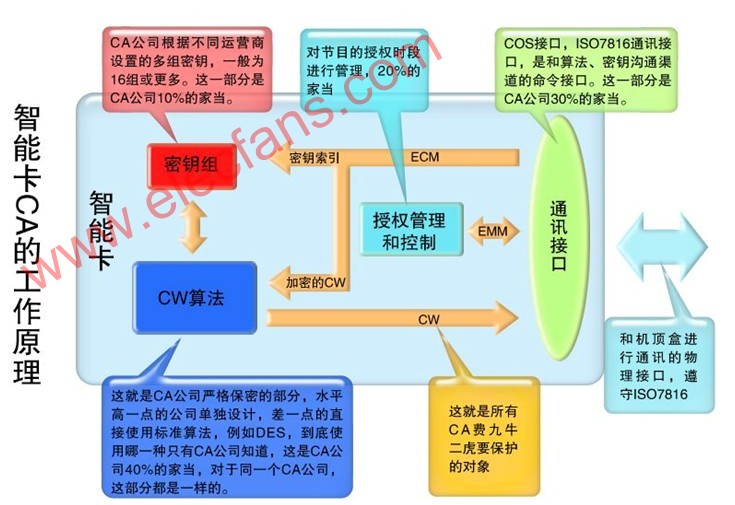
Figure 1 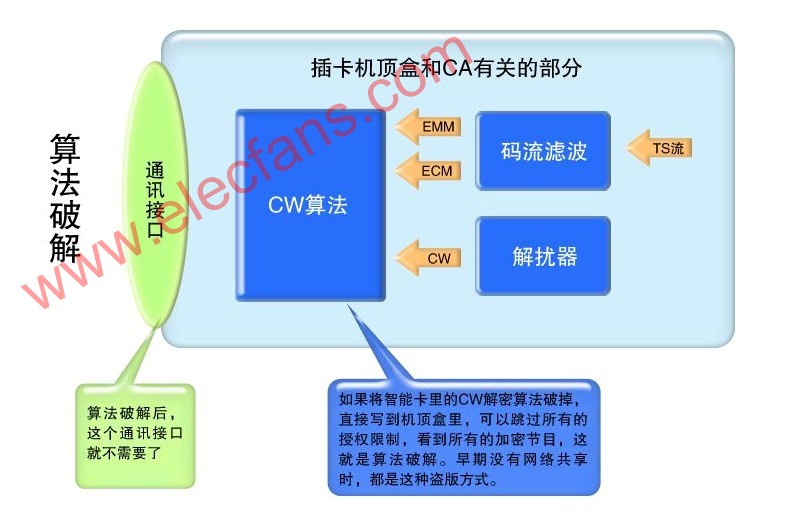
Figure II 
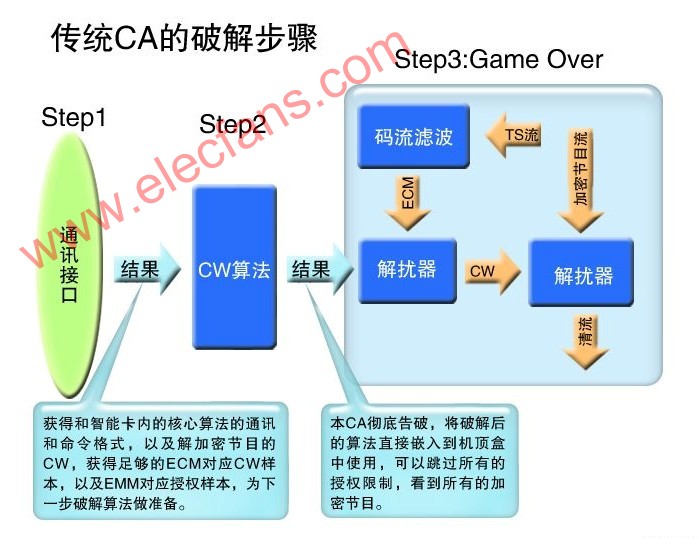
The working principle of digital TV smart card CA
Recently, the security of digital TV CAs has been discussed vigorously. From the perspective of popular digital TV sharing technologies in Europe and America, the author uses diagrams to add text to show everyone a mysterious digital TV CA in front of readers.